If you don’t think a company’s tech matters, think again. This is the single biggest risk and hidden cost when it comes to making your day one target and realizing the cost savings you were banking on with the acquisition.
Permanent Strangulation
When discussing how to transition to new systems or environments, one of my favorite approaches is the strangler pattern because it allows for a low risk approach to transition to the new environment in a piecemeal fashion. There is a hidden risk with this approach, and it is the price tag is increased tech debt adding complexity and maintenance costs. …
Upselling and Breaking Up with BigCo
I was talking with my client the other day as they were looking to replace their web gateway from the early 2000s with an enterprise version of an open-source alternative. This client had a long-standing relationship with BigCo, but wasn’t really happy with them. My client’s previous attempt to escape for a smaller vendor with a much better offering and …
Strangling Your Data
A while ago, I wrote a post looking at different ways to modernize an application while retaining preexisting functionality. One of these techniques is called the strangler patterns which gets its name from the strangler fig. The idea being: In the original post, I highlighted two techniques that can be used to replicate data: one from a web proxy standpoint, …
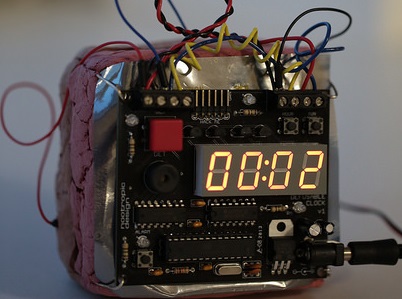
Do You Have A Time Bomb in Your Data Center Waiting to Go Off?
Every organization has at least one. The black box in the corner, that few understand, and even fewer that want to touch. It hums along for years powering the critical parts of the business. It contains the crown jewels of your enterprise. When it goes down, so does your business, but is it a time bomb waiting to go off? …
Digital Transformation and Talent
Digital Transformation is a hot topic. Prior to the world changing due to the pandemic, it was integrating AI and machine learning assist with automating the risk calculations during policy underwriting or fraud detection when claims are filed. During the pandemic, the focus changed to the user experience for the agents, underwriters, adjusters, and even the customers facilitating remote work …
The Anti-Corruption Pattern and Legacy Migration Strategies
Wrapping up the posts on Legacy Migration Strategies, this article will focus on the Anti-Corruption Pattern. The anti-corruption pattern describes some custom code to interface between a legacy application and a new target application. The reason why the pattern is called anti-corruption, is due to the corruptive nature of new development being forced to conform to a pre-defined legacy interface. …
The Strangler Pattern and Legacy Migration Strategies
Following up on my previous post on Legacy Migration Strategies, I will be talking about the strangler pattern. At its core, the approach is to take your original application, and replace it piece-by-piece by “strangling” it to death with each new component. The biggest reason for architecting with this approach in mind is to minimize the impact of the transition …